Appreciate the reply, cheers.We don't know exactly what the bug is or exactly how Denuvo/VMProtect work but it appears that kernel system calls are where the performance hits are. Denuvo/VMProtect probably implement virtual machine techniques but I don't think they do so through kernel modules or kernel drivers, so ideally they won't be effected too much unless their virtual machine environments do a lot of kernel system calls. If they do I/O a lot then they might. If not, then probably the same impact as any other game.
-
Ever wanted an RSS feed of all your favorite gaming news sites? Go check out our new Gaming Headlines feed! Read more about it here.
-
We have made minor adjustments to how the search bar works on ResetEra. You can read about the changes here.
Intel CPUs Affected By Kernel Memory Bug, Possible Slowdown Coming
- Thread starter TC McQueen
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
As far as I know dolphin must keep the emulated CPU and GPU threads synched, stopping one so that it doesn't gets ahead of the other by too much and viceversa.console emulators probably not much, those are usually software based. Hardware virtualized emulators like Nox and Memu should get hit.
Expect future intel processors to have the bugs fixed, btw
Probably those interrupts will suffer the performance hit if I am understanding this correctly.
I bought an i7 6700 a year ago and now it will lose 30% of it's performance?
Nice.
Same here.wtf
Ah I didn't go digging through the patches so I didn't see that. However end users can often have paravirtualization enabled for stuff like VirtualBox or other virtual machine software, not just hypervisors.Just as an FYI the kaiser code is activated under the following conditions
PARAVIRT = software virtualization
!PARAVIRT = hardware virtualization
So reading this it says it's active on 64 bit x86 CPUs when any virtualization is not done entirely by software (read HW virtualization)
I don't see any kind of checking for AMD vs Intel so I'd assume both will get hit if HW-VT is turned on which means Azure and EC2 will take a big hit.
Ah I didn't go digging through the patches so I didn't see that. However end users can often have paravirtualization enabled for stuff like VirtualBox or other virtual machine software, not just hypervisors.
But it's definitely some combination of buggy hypervisor + preemption. Unfortunately, recentish intel processors have hardware virtualization turned on by default and telling non-tech people how to go into the bios to disable it if it's possible is probably the worse road to take compared to KPTI so here we are.
It appears 64-bit ARM Linux kernels will also get a set of KAISER patches, completely splitting the kernel and user spaces, to block attempts to defeat KASLR.
The ARM patch shows updates to hypercall.S hmm. Yea, this bug is tied to some problem in hardware virtualization. It's a little bit interesting that both ARM and Intel processors exhibited similar but different bugs in their virtual memory handling under the hypervisor. ( note depending on how you set up the os and how your bios is configured you could be running under a hypervisor even though you're not running under a VM )
With the current patch info, ARM and all X86-64 processors that have HW-VT enabled would be hit though there's still time to update to do some CPU checking. It probably won't be done as it would clutter the code base.
With the current patch info, ARM and all X86-64 processors that have HW-VT enabled would be hit though there's still time to update to do some CPU checking. It probably won't be done as it would clutter the code base.
Wow with so many servers being virtualized these days the up to 30% hit is really going to piss off a lot of business customers.
Hey, I'm trying to catch up, can someone tell me what exactly is incorrect in the mod edit, so I can correct it?
Reading through the kaiser patch, I'd suggest letting the mod edit stand for now though we do have new information showing the linux kernel for ARM also needed the KAISER patch suggesting at least some ARM variants suffer the same flaw as Intel's processors. That flaw looks to be in the hypervisor.
I'm not even sure how to imagine what datacenter providers are going to do to handle this, or what will happen to any customer using them, i.e. Google Compute, Amazon EC2, Microsoft Azure. Datacenter capacity was always a huge problem in my time at Microsoft, and was constantly being addressed and increased to meet demands daily. Capacity forecasting, prediction, management, purchasing, etc. They're going to be impacted the hardest by this, and I'm trying to imagine what kind of nightmare it is there right now knowing that the moment they roll out the security patch for this their capacity will suddenly undergo a hard drop up to 30%. How will the end users on the cloud be affected, businesses, services, websites, all of them that met certain levels of capacity will now be over capacity and unable to meet the workload. How are the cloud providers going to distribute the load the meet the sudden capacity change, or how they will charge users for the capacity in-use. What's going to happen to future orders for new hardware to increase capacity, which now no longer meet their initial estimations for capacity growth.
I can't even process how they will go about handling this, this a nightmare.
I can't even process how they will go about handling this, this a nightmare.
Edit: That mod edit in the OP is wrong if you're reading this... It is NOT limited to virtualized machines.
Yeah, I asked someone who had been following this and they said the same thing. Affects everything.
And since newer Intel CPUs can't run on W8.1 (without hacks) users of that OS are kinda screwed there, too.
Doom 2016 last time I checked.
You should know post vulkan linux via wine is insanely good. Even through emulation you can get more stable dpc latency times due to fact linux doesn't have a bad as cpu scheduler or network stack which can lead to more reponsive cpu performance considering overhead and bloat aren't eating it anymore.
There are youtube videos of it running on Ubuntu on 1070 GTX or similar powerful cards.
I dun care if I am af fffected. I ain't giving muh 2600K up.Also affected.
At this point ResetERA needs Reddit like threading because people just aren't getting the message. One false post leads to 1000 propagations.
Just as an FYI the kaiser code is activated under the following conditions
PARAVIRT = software virtualization
!PARAVIRT = hardware virtualization
So reading this it says it's active on 64 bit x86 CPUs when any virtualization is not done entirely by software (read HW virtualization)
I don't see any kind of checking for AMD vs Intel so I'd assume both will get hit if HW-VT is turned on which means Azure and EC2 will take a big hit.
Not quite.
You're quoting the Kernel build configuration, which is a compile-time (not run-time) directive. It simply means that you can't enable paravirtualization support and KAISER at the same time. They're mutually exclusive.
This has nothing to do with whether or not the CPU supports VT-X, or whether or not the kernel uses those features.
Yeah, I asked someone who had been following this and they said the same thing. Affects everything.
And since newer Intel CPUs can't run on W8.1 (without hacks) users of that OS are kinda screwed there, too.
No, the source code patches themselves are pretty explicitly clear about when the KAISER code is executed. When running under an X86-64 hypervisor or a 64-bit ARM hypervisor, the KAISER code is active. Otherwise, the KAISER code is inactive. Now, most modern intel processors have HW-VT turned on by default in the bios and Windows doesn't really give you a choice as far as I know and basically obeys your BIOS(we won't really know how MS tackles it but we do know the Linux solution). Linux on the other hand allows you to choose to turn off HW-VT support in the kernel.
Not quite.
You're quoting the Kernel build configuration, which is a compile-time (not run-time) directive. It simply means that you can't enable paravirtualization support and KAISER at the same time. They're mutually exclusive.
This has nothing to do with whether or not the CPU supports VT-X, or whether or not the kernel uses those features.
The ARM patch directly patches the Xen hypercall.S file suggesting it is indeed inside of the hypervisor that the KAISER code is calling.
AMD's statement only tells us that they are not subject to the bug. It doesn't say that they won't be affected by the fix that OS makers will put in place. It depends on whether they decide to only implement the change for Intel processors or if they do it universally.
There's already a commit made in the Linux kernel to skip the fix for AMD processors:
Disable page table isolation by default on AMD processors by not setting
the X86_BUG_CPU_INSECURE feature, which controls whether X86_FEATURE_PTI
is set.
https://lkml.org/lkml/2017/12/27/2
There's already a commit made in the Linux kernel to skip the fix for AMD processors:
https://lkml.org/lkml/2017/12/27/2
The commit has also been reviewed and accepted, although it has not been merged into a release yet.
Preliminary performance numbers in Linux... uh, wow...
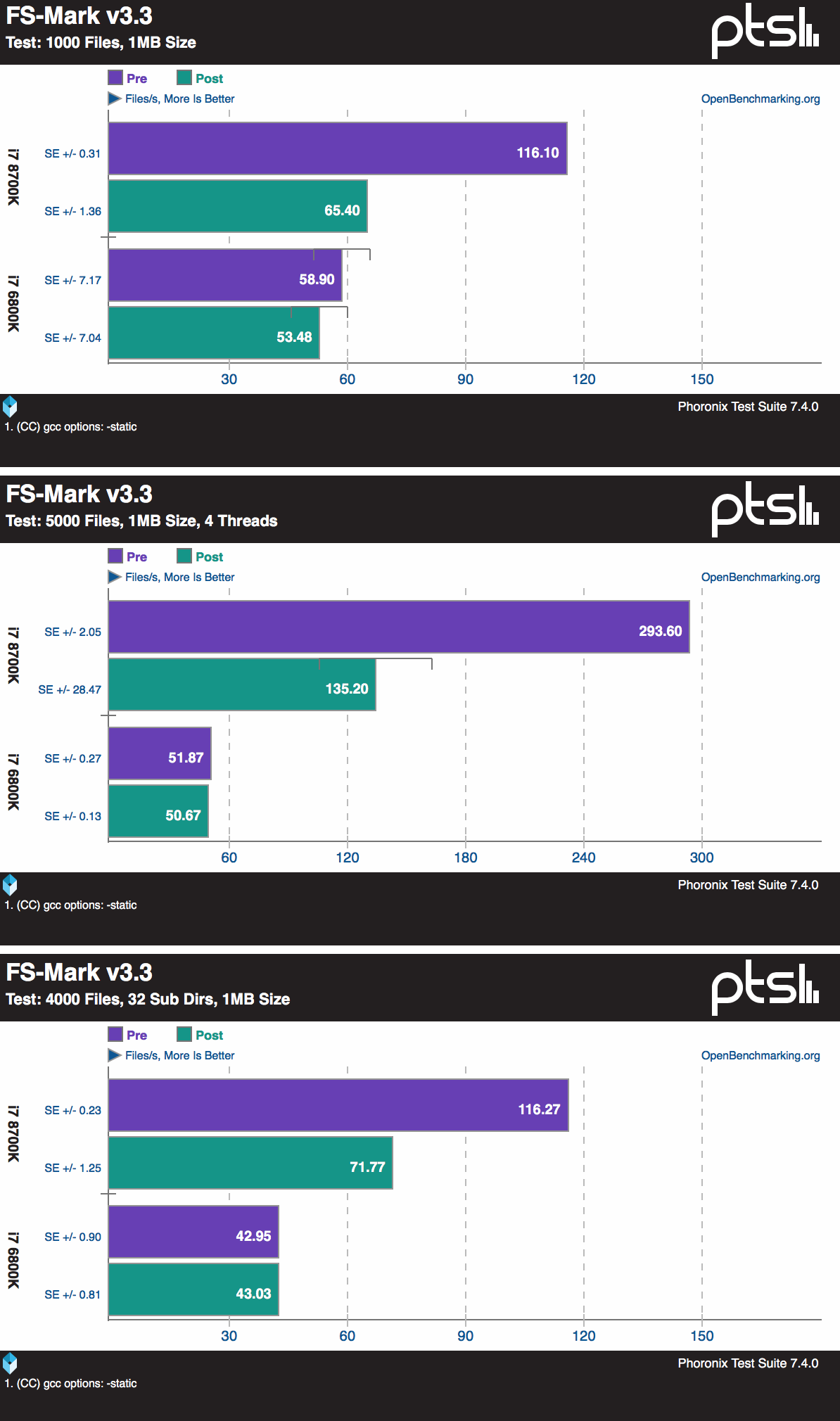
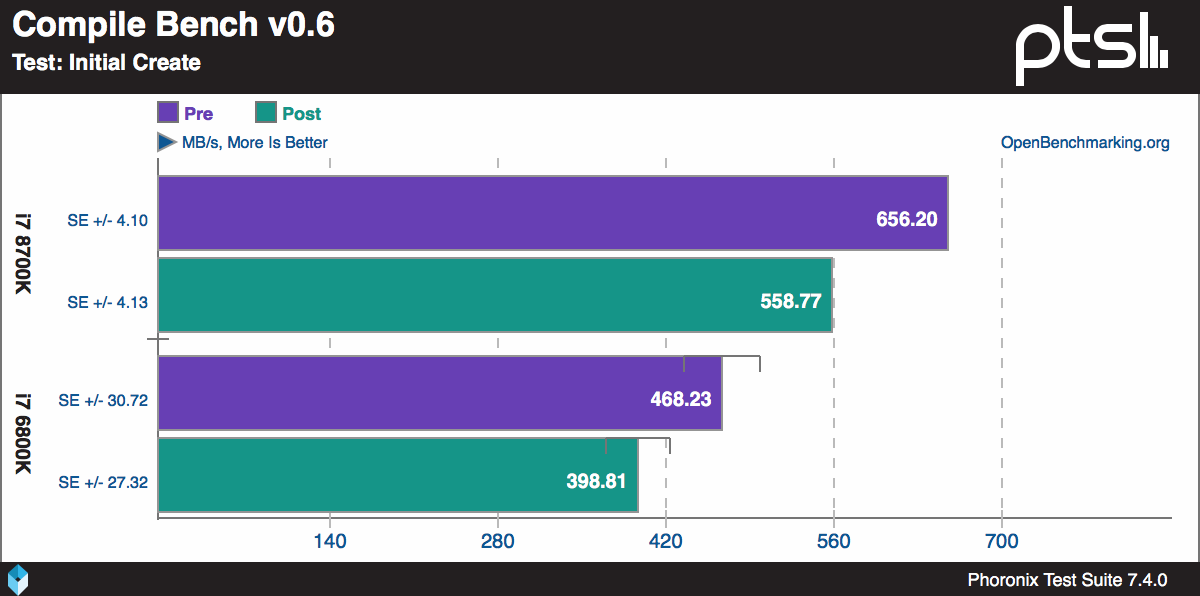
https://www.phoronix.com/scan.php?page=article&item=linux-415-x86pti&num=2
Other areas like video encoding don't seem to be affected at all, but holy shit.


https://www.phoronix.com/scan.php?page=article&item=linux-415-x86pti&num=2
Other areas like video encoding don't seem to be affected at all, but holy shit.
Yeah, FYI for AMD users: https://www.phoronix.com/scan.php?page=news_item&px=x86-PTI-EPYC-Linux-4.15-TestThe commit has also been reviewed and accepted, although it has not been merged into a release yet.
But at least for now the mainline kernel is still treating AMD CPUs as "insecure" and is too taking a performance hit.
Over one week later, that patch has yet to be merged to the mainline kernel. When booting the Linux 4.15 kernel on an AMD EPYC box, indeed, for now the AMD CPU is still treated with a bug of "insecure_cpu."
An immediate workaround at least until the AMD patch lands where PTI isn't applied to AMD CPUs is by booting the kernel with the nopti kernel command-line parameter. This can also be applied to Intel systems too on a patched kernel if wanting to regain the performance and are not too concerned about this vulnerability.
Very long thread, don't have the time to read everything. I have an i5 6600K, am I affected by this?
Preliminary performance numbers in Linux... uh, wow...


https://www.phoronix.com/scan.php?page=article&item=linux-415-x86pti&num=2
Other areas like video encoding don't seem to be affected at all, but holy shit.
Ok thats unacceptable.
Yep Ryzen is a godsend. Raven Ridge can't come soon enough so I can replace my laptop too and be Intel free.I was already really happy with my Ryzen 1700. This only solidifies that.
Very long thread, don't have the time to read everything. I have an i5 6600K, am I affected by this?
You're affected by this in the abstract. Do you do a lot of IO intensive (read/writes to hard drives) tasks? Then, it will impact you. For gaming, benchmarks show it has little to no impact on GPU and CPU bound tasks.
+ * On Intel CPUs, if a SYSCALL instruction is at the highest canonical
+ * address, then that syscall will enter the kernel with a
+ * non-canonical return address, and SYSRET will explode dangerously.
+ * We avoid this particular problem by preventing anything executable
+ * from being mapped at the maximum canonical address.
+ *
+ * On AMD CPUs in the Ryzen family, there's a nasty bug in which the
+ * CPUs malfunction if they execute code from the highest canonical page.
+ * They'll speculate right off the end of the canonical space, and
+ * bad things happen. This is worked around in the same way as the
+ * Intel problem.
+ *
+ * With page table isolation enabled, we map the LDT in ... [stay tuned]
Just also as an FYI for those running Ryzen and maybe why AMD's code didn't get merged into the mainstream.
It's either unrelated or not the "real" advisory.
eh, one of the patches is to arm64/xen/hypercall.S
There's a decent chance that this is the embargoed CVE.
Just also as an FYI for those running Ryzen and maybe why AMD's code didn't get merged into the mainstream.
In case people are curious, the source is this email on the lkml: https://lkml.org/lkml/2017/12/28/748 .
I believe you're misinterpreting the comment, however. It's explaining why the user space process size is calculated the way it is. It has nothing directly to do with this vulnerability, or the PTI changes. Notably, while the explanation for the calculation was expanded upon, this patch does not change the calculation itself.
Preliminary performance numbers in Linux... uh, wow...


https://www.phoronix.com/scan.php?page=article&item=linux-415-x86pti&num=2
Other areas like video encoding don't seem to be affected at all, but holy shit.
File system access time destroyed on the SSD. I wonder if HDD speeds remain about the same considering how lethargic HDDs are anyways.
This wouldn't be related to anything happening right now, would it?
https://www.fool.com/investing/2017/12/19/intels-ceo-just-sold-a-lot-of-stock.aspx
Smells like insider trading Well, I hope it doesn't bite me in the ass too. I really hope it's a window for AMD, fate has opened an opportunity
Is your chip ten years old or less? Is it Intel? Yes? Congrats, you're affected.Very long thread, don't have the time to read everything. I have an i5 6600K, am I affected by this?
Tom from AMD already posted the exclusion on the 27th https://lkml.org/lkml/2017/12/27/2 but I'm not sure if it got merged yet.
edit: I'm not holding my breath that this will get merged before the embargo ends. They're working non-stop to get the fix out ASAP.
The base model iMac Pro is a 3.2 8-core chip (vs. 3.6 quad-core for the current top-of-the-line consumer iMac).I'm a graphic designer and our whole office uses iMacs instead of the pros because they have faster single-core clock speeds
Now, frequency goes down as cores go up, so you obviously wouldn't get an 18-core system for workloads that aren't heavily parallelized, but a base iMac Pro should still have considerably more leg room with relatively little tradeoff (of course, the cost associated likely outweighs the benefit unless you're really going to put it to work).
So jediyoshi caught this in the Steam thread:
https://hothardware.com/news/intel-cpu-bug-kernel-memory-isolation-linux-windows-macos
The article says:
"As it turns out, apparently the Linux patch that is being rolled out is for ALL x86 processors including AMD, and the Linux mainline kernel will treat AMD processors as insecure as well. As a result, AMD CPUs will feel a performance hit as well, though the bug only technically affects Intel CPUs and AMD recommends specifically not to enable the patch for Linux. How Microsoft specifically will address the issue with the Windows operating system remains unclear until the company's formal Patch Tuesday update is made known, hopefully soon."
So it's a generalised patch. Now in Linux, it's very common for admins to apply only relevant patches. MS, especially in the Win10 era, has been known to push patches aggressively. Hopefully even if MS decides to force a patch, they'll provide a tool for "power users" with AMD chips to disable.
https://hothardware.com/news/intel-cpu-bug-kernel-memory-isolation-linux-windows-macos
The article says:
"As it turns out, apparently the Linux patch that is being rolled out is for ALL x86 processors including AMD, and the Linux mainline kernel will treat AMD processors as insecure as well. As a result, AMD CPUs will feel a performance hit as well, though the bug only technically affects Intel CPUs and AMD recommends specifically not to enable the patch for Linux. How Microsoft specifically will address the issue with the Windows operating system remains unclear until the company's formal Patch Tuesday update is made known, hopefully soon."
So it's a generalised patch. Now in Linux, it's very common for admins to apply only relevant patches. MS, especially in the Win10 era, has been known to push patches aggressively. Hopefully even if MS decides to force a patch, they'll provide a tool for "power users" with AMD chips to disable.
This will impact some of my clients if the virtualization performance loss estimates are accurate. I can't imagine how the peeps at AWS / Azure / etc. are going to handle this capacity planning nightmare.
Intel is reaping what it sowed and I'll shed no tears over the misfortune.
Intel is reaping what it sowed and I'll shed no tears over the misfortune.
You're affected by this in the abstract. Do you do a lot of IO intensive (read/writes to hard drives) tasks? Then, it will impact you. For gaming, benchmarks show it has little to no impact on GPU and CPU bound tasks.
Is your chip ten years old or less? Is it Intel? Yes? Congrats, you're affected.
Although I put my PC together myself, I'm no expert. All I do is play games and download games to my hard disk and SSD, sometimes I transfer games from one drive to the other.
So what you're saying is that processes like these would be affected but my gaming shouldn't be?
Literally scroll up https://www.resetera.com/threads/up...ble-slowdown-coming.13923/page-8#post-2776465So jediyoshi caught this in the Steam thread:
https://hothardware.com/news/intel-cpu-bug-kernel-memory-isolation-linux-windows-macos
The article says:
"As it turns out, apparently the Linux patch that is being rolled out is for ALL x86 processors including AMD, and the Linux mainline kernel will treat AMD processors as insecure as well. As a result, AMD CPUs will feel a performance hit as well, though the bug only technically affects Intel CPUs and AMD recommends specifically not to enable the patch for Linux. How Microsoft specifically will address the issue with the Windows operating system remains unclear until the company's formal Patch Tuesday update is made known, hopefully soon."
So it's a generalised patch. Now in Linux, it's very common for admins to apply only relevant patches. MS, especially in the Win10 era, has been known to push patches aggressively. Hopefully even if MS decides to force a patch, they'll provide a tool for "power users" with AMD chips to disable.
I edited out the original mod post on the first page to make sure the reasoning for the thread move is clear and so that the potential for misinformation as more tests are done aren't caused.
Thank you.
This will impact some of my clients if the virtualization performance loss estimates are accurate. I can't imagine how the peeps at AWS / Azure / etc. are going to handle this capacity planning nightmare.
Intel is reaping what it sowed and I'll shed no tears over the misfortune.
You mean to tell me that security through obscurity doesn't work? /s
So jediyoshi caught this in the Steam thread:
https://hothardware.com/news/intel-cpu-bug-kernel-memory-isolation-linux-windows-macos
The article says:
"As it turns out, apparently the Linux patch that is being rolled out is for ALL x86 processors including AMD, and the Linux mainline kernel will treat AMD processors as insecure as well. As a result, AMD CPUs will feel a performance hit as well, though the bug only technically affects Intel CPUs and AMD recommends specifically not to enable the patch for Linux. How Microsoft specifically will address the issue with the Windows operating system remains unclear until the company's formal Patch Tuesday update is made known, hopefully soon."
So it's a generalised patch. Now in Linux, it's very common for admins to apply only relevant patches. MS, especially in the Win10 era, has been known to push patches aggressively. Hopefully even if MS decides to force a patch, they'll provide a tool for "power users" with AMD chips to disable.
The Xbox uses an AMD processor. I don't know how much code is in common between Windows and the Xbox, but I'd guess it's the same kernel. So surely they'd architect their fix in a way that doesn't hurt AMD performance.
- Status
- Not open for further replies.

